>>_

Modded Android applications such as InstaPro, Spotify pro, and other “Pro” variants have become one of the most effective malware delivery mechanisms in civilian environments. Unlike traditional malware, these apps do not rely on exploits or vulnerabilities; instead, they exploit user trust. Distributed via third-party websites and messaging platforms, modded apps promise premium features but operate outside Android’s security and integrity guarantees. In countries like India, where sideloading APKs is common, this creates a high-risk environment where ordinary users unknowingly install tampered software capable of long-term surveillance, data theft, and financial fraud.https://www.kaspersky.com/about/press-releases/kaspersky-report-attacks-on-smartphones-increased-in-the-first-half-of-2025
From an OS-level perspective, modded apps aggressively abuse Android’s permission model. These applications commonly request SMS, Notification access, media storage, phone state, and Accessibility permissions — a combination sufficient to intercept OTPs, read messages, capture screen content, and fingerprint devices. Many register boot receivers and foreground services to ensure persistence across reboots. Once installed, the app continuously communicates with remote servers, effectively functioning as a command-and-control client rather than a benign application.
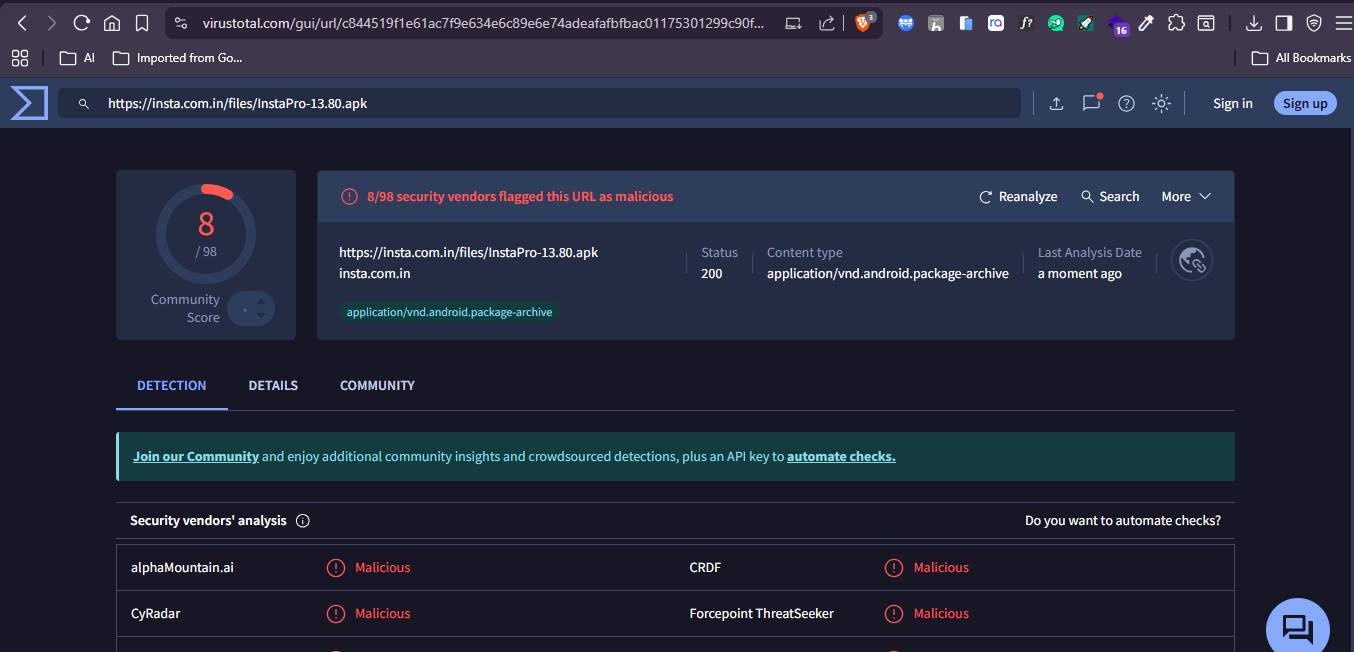
A defining trait of modded-app ecosystems is the use of fake trust signals. Download pages prominently display claims such as “100% Safe,” “Security Verified,” and antivirus logos to manipulate user perception. These indicators are purely visual and have no cryptographic or technical backing. Independent verification using malware-scanning platforms frequently contradicts these claims, revealing that the same APKs are flagged as malicious by multiple security vendors. This gap between marketing and reality is a deliberate social-engineering strategy.

 A common misconception is that an APK is safe if only a few antivirus engines detect it. In mobile malware analysis, this logic is flawed. Modern Android malware uses obfuscation, custom packers, and delayed execution to evade static detection. As a result, early detections are often limited to behavioral or heuristic engines. When a sideloaded social-media app is flagged by even a small number of reputable vendors, it is a strong indicator of real risk — not a false positive.
A common misconception is that an APK is safe if only a few antivirus engines detect it. In mobile malware analysis, this logic is flawed. Modern Android malware uses obfuscation, custom packers, and delayed execution to evade static detection. As a result, early detections are often limited to behavioral or heuristic engines. When a sideloaded social-media app is flagged by even a small number of reputable vendors, it is a strong indicator of real risk — not a false positive.
Modded APKs are rarely discovered organically; they are actively pushed through WhatsApp messages, Telegram channels, fake ads, and SEO-optimized download pages. Attackers use urgency-based messaging such as “Account verification required” or “New update mandatory” to pressure users into sideloading. Localization — including Indian languages and familiar branding — increases credibility. This method bypasses technical defenses entirely by manipulating human behavior first.https://timesofindia.indiatimes.com/technology/tech-news/hdfc-bank-warns-against-apk-fraud-what-is-it-and-how-it-works/articleshow/123135988.cms.Accessibility Services are one of the most abused Android features in malicious modded apps. Once granted, an app can read screen content, observe keystrokes, auto-approve permissions, and overlay fake UI elements. This enables OTP interception, credential theft, and silent interaction with banking and payment apps. Many real-world fraud victims report never sharing OTPs — technically true, because the malware accessed them directly via Accessibility.
Instagram and messaging-app mods are especially valuable to attackers because they function as trust amplifiers. Compromised accounts can be used to spread phishing links, scam messages, and malicious APKs to known contacts. This enables exponential propagation, turning a single infected device into a distribution node for secondary attacks.https://www.mcafee.com/blogs/other-blogs/mcafee-labs/android-malware-targets-indian-banking-users-to-steal-financial-info-and-mine-crypto.Modded APKs are typically distributed without signed update channels, public hashes, or reproducible builds. Users cannot verify whether an update contains new features or a malicious payload. This creates a supply-chain risk similar to compromised update servers, allowing attackers to silently swap binaries or selectively target users.
Many modded apps act as droppers rather than full malware packages. The visible APK downloads or activates the malicious payload only after specific triggers such as time delays, location checks, or remote commands. This explains why antivirus results can change days or weeks after installation and why initial “clean” scans are unreliable.Indian news reports repeatedly document cases where civilians lose lakhs of rupees after installing fake APKs posing as updates or financial tools. These incidents demonstrate that modded apps cause real financial and psychological damage, not just theoretical risk.https://timesofindia.indiatimes.com/city/hyderabad/fake-apk-apps-drain-rs-11-lakh-from-three-hyderabad-residents/articleshow/126097259.cms?utm_source=chatgpt.comhttps://timesofindia.indiatimes.com/city/ahmedabad/hacked-2-0-it-gets-appsolutely-dangerous-when-crime-goes-mobile-in-gujarat/articleshow/125284165.cms?utm_source=chatgpt.com
Modded Android applications should not be viewed as harmless shortcuts or personal customizations; they must be treated as untrusted software with active threat potential. By design, these apps break platform integrity, bypass security controls, and operate outside any accountable update or disclosure framework. For civilians, this translates directly into increased risk of financial fraud, account takeover, and irreversible privacy loss. For developers and platforms, it creates a hostile client environment where abuse becomes indistinguishable from legitimate usage. The security conclusion is straightforward: no amount of free features justifies surrendering device trust. Avoiding sideloaded social-media and financial apps is not a best practice anymore — it is a minimum requirement for digital safety.
